Installation
- Docker
- K8S
- EKS (Terraform)
Before installing Lunar's Proxy, make sure that Docker is installed on your environment. If you haven't installed Docker yet, you can learn more about it and download it from the Docker website
Installation through the Lunar Control Plane
The easiest installation process is through the Lunar Control Plane. After launching the control plane, simply follow the step-by-step instructions that appear after clicking the "Continue" button. As long as you have a Docker instance up and running, the Lunar Control Plane will be automatically synced to your proxy via the API key that appears in the command for you to copy.

Manual Installation
Alternatively, if you do not want to leverage the Lunar Control Plane, you can install the Lunar Proxy without the UI by following the steps below.
Step 1: Run Lunar's Proxy Container
Once the image download is complete, you can run the proxy container using the following command:
docker run -d --rm -p 8000:8000 -p 8081:8081 -p 8040:8040 -e TENANT_NAME="ORGANIZATION" -v $(pwd):/etc/lunar-proxy --name lunar-proxy lunarapi/lunar-proxy:latest
Note that the TENANT_NAME environment variable is required. This variable should be set to the name of your organization.
-d: Start a container in detached mode.
--rm: Automatically remove the container when it exits.
-p: Publish all exposed ports to the host interfaces.
-e: Set environment variables. In this case, we set the TENANT_NAME environment variable to ORGANIZATION.
-v: Flag in your Docker run command to mount your local policies.yaml file to the /etc/lunar-proxy directory inside the Lunar Proxy container.
--name: The UUID identifiers come from the Docker daemon.
Step 2: Verify Installation
To ensure the successful installation of Lunar Proxy there are two options:
Option 1: Run the following command to make a request to the healthcheck endpoint which validates that Lunar Proxy is up.
curl http://localhost:8040/healthcheck
Or, if you prefer using wget:
wget -qO - http://localhost:8040/healthcheck
Please note that these commands are interchangeable based on your preference and the availability of curl or wget on your system.
Option 2: Try to pass a request through the proxy by running the following command:
curl http://localhost:8000/fact -H "x-lunar-host: catfact.ninja" -H "x-lunar-scheme: https"
Or, with wget:
wget -qO - --header="x-lunar-host: catfact.ninja" --header="x-lunar-scheme: https" http://localhost:8000/fact"
This will make a request to Lunar Proxy on port 8000, which will forward the request to the upstream server catfact.ninja on port 443, at the path /fact (this is an API that returns the latest exchange rates).
The result should look something like this:
{"fact":"Among many other diseases, cats can suffer from anorexia, senility, feline AIDS and acne.","length":89}
Then, use the discover command to validate that the requests were passed through Lunar Proxy.
docker exec lunar-proxy discover
The result should look something like this:
{
"interceptors": [
{
"type": "unknown",
"version": "unknown",
"last_transaction_date": "2023-07-10T08:56:12Z"
}
],
"endpoints": {
"GET:::catfact.ninja/fact": {
"min_time": "2023-02-05T17:07:42",
"max_time": "2023-02-05T17:09:14",
"count": 1,
"status_codes": {
"200": 1
},
"average_duration": 555
}
}
}
The interceptor type and version are unknown because we are using curl to make the request. Once an interceptor is used, its type and version will appear in the discover command output.
For more information about the Discover command, see discover.
Before installing Lunar's Proxy, make sure that Helm is installed on your environment. If you haven't installed Helm yet, you can learn more about it and download it from the Helm website
Installation through the Lunar Control Plane
The easiest installation process is through the Lunar Control Plane. After launching the control plane, simply follow the step-by-step instructions that appear after clicking the "Continue" button. As long as you have Helm installed, the Lunar Control Plane will be automatically synced to your proxy via the API key that appears in the command for you to copy.

Manual Installation
Alternatively, if you do not want to leverage the Lunar Control Plane, you can install the Lunar Proxy without the UI by following the steps below.
Step 1: Add and update Lunar repository
To start the installation process, add and update our Lunar Proxy repository for helm charts. ֿOpen a terminal or command prompt and execute the following command:
helm repo add lunar https://thelunarcompany.github.io/proxy-helm-chart/
helm repo update
Step 2: Override Lunar Proxy configuration (Optional)
if you need to override values in the Lunar Proxy chart, you can get the default values.
helm show values lunar/lunar-proxy | tee values.yaml
Step 3: Install Lunar Proxy helm chart
Once you have the updated values.yaml file, you can proceed to install the Lunar Proxy chart using the following command:
- In case of default installation
helm install lunar-proxy lunar/lunar-proxy --set tenantName=<name> --namespace lunar-proxy --create-namespace
Before installing Lunar's Proxy, ensure that the tenantName is set to the name of your organization, for example: Acme or Google.
tenantName - is a mandatory requirement, Lunar Proxy will not start if it is left unset.
This can also be set in the values.yaml file.
- In case of changes in the
values.yaml
helm install lunar-proxy lunar/lunar-proxy -f values.yaml
Step 4: Verify Installation
To ensure the successful installation of Lunar Proxy there are two options:
Option 1: Run the following command to make a request to the healthcheck endpoint which validates that Lunar Proxy is up.
helm test lunar-proxy
Option 2: Try to pass a request through the proxy by running the following command:
curl http://localhost:8000/fact -H "x-lunar-host: catfact.ninja" -H "x-lunar-scheme: https"
This will make a request to Lunar Proxy on port 8000, which will forward the request to the upstream server catfact.ninja on port 443, at the path /fact (this is an API that returns the latest exchange rates).
The result should look something like this:
{"fact":"Among many other diseases, cats can suffer from anorexia, senility, feline AIDS and acne.","length":89}
Then, use the discover command to validate that the requests were passed through Lunar Proxy.
kubectl exec <lunar-proxy-pod-name> -- discover
The result should look something like this:
{
"interceptors": [
{
"type": "unknown",
"version": "unknown",
"last_transaction_date": "2023-07-10T08:56:12Z"
}
],
"endpoints": {
"GET:::catfact.ninja/fact": {
"min_time": "2023-02-05T17:07:42",
"max_time": "2023-02-05T17:09:14",
"count": 1,
"status_codes": {
"200": 1
},
"average_duration": 555
}
}
}
The interceptor type and version are unknown because we are using curl to make the request. Once an interceptor is used, its type and version will appear in the discover command output.
For more information about the Discover command, see discover.
Installation through the Lunar Control Plane
The easiest installation process is through the Lunar Control Plane. After launching the control plane, simply follow the step-by-step instructions that appear after clicking the "Continue" button. As long as you have a Docker instance up and running, the Lunar Control Plane will be automatically synced to your proxy via the API key that appears in the command for you to copy.
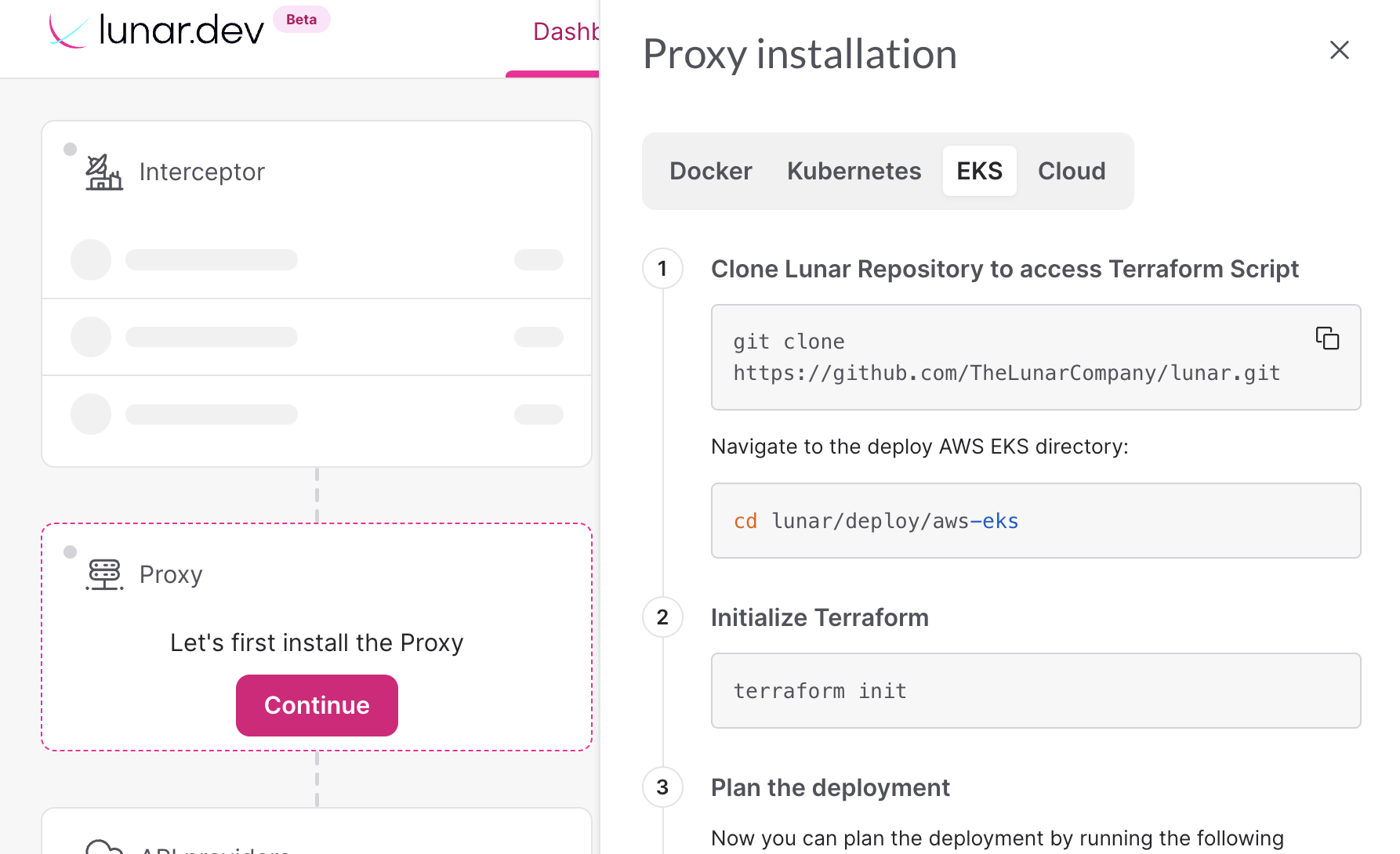
Manual Installation
Using the terraform script here, you can deploy the Lunar Proxy on an AWS EKS cluster.
Step 1: Clone the Lunar Proxy repository
Clone the Lunar Proxy repository to your local machine:
git clone https://github.com/TheLunarCompany/lunar.git
Step 2: Navigate to the Terraform directory
Navigate to the deploy AWS EKS directory:
cd lunar/proxy/deploy/aws-eks
Step 3: Initialize the Terraform directory
terraform init
Step 4: Plan the deployment
Some variables are mandatory and their values must be supplied. You can supply them in the command dialog or as the command input variables.
The following variables must be provided:
input_eks_name- The EKS cluster nameinput_tenant_name- Your organization's name (e.g. Google, Acme)
Your eks nodes should allow inbound traffic from the created Network Load Balancer on the EKS public subnets. Ports 8000, 8040 and 8081 should have an allow rule. If you do not have such a rule. specifying the security group of your eks nodes (security_group_nlb_2_nodes) is needed to add the rule by the Terraform.
Some variables have default values. These can be overridden in the command input variables or in the variables.tf file.
The following variables can be modified:
aws_profile_name- defaults to "default" - Add this value to use a specific aws profile. you can see the local profile names at~/.aws/confighelm_chart_repository- defaults to "" - Change this if you want to use a private repository with a different pathhelm_chart_name- defaults to "lunar-proxy" - Change this if you want to use a private chart with a different namehelm_chart_version- defaults to "latest" - Change this if you want to use a specific version.
helm_releasewill not automatically grab the latest release, version must explicitly upgraded when upgrading an installed chart.lunar_api_key- defaults to "" - The Lunar API key to integrate with the Control Plane (Optional, get your API key by signing in to the Lunar Control Plane)lunar_api_key_secret_name- defaults to "" - The name of the secret, which will contain the Lunar API key to integrate with the Control Plane. The value of the API key must be in the given secret under the keylunarAPIKeysecurity_group_nlb_2_nodes- defaults to "skip" - Add this in case there is no rule allowing from the nlb subnets to the nodes TCP on ports 8000, 8040 & 8081, if this value is not provided, then setting the rules will be skipped.
You can run the following command to plan the deployment (for example):
terraform plan -input=true -var 'input_tenant_name=exampleTenant' -var 'input_eks_name=exampleEksName'
Step 5: Run Terraform
terraform apply -input=true
To get the output traces:
terraform output
To clean and remove the resources.
terraform destroy -input=true
The following changes will be made:
- The proxy is deployed using the specific release helm chart.
- The Network Load Balancer is set to forward traffic to the proxy.
- The security groups needed to allow network traffic are set (Allow ports 8000,8081,8040 inbound and all outbound).