Agent Access Control
The Tool Access in the Agent modal in MCPX lets you manage which tools and services each agent can use. It provides a simple toggle-based interface for granting or restricting access without editing configuration files.
Overview
Every agent has an access control section that defines its tool permissions. You can grant full access to all tools or limit access to specific tool groups created in your Tool Catalog.
This makes it easy to maintain fine-grained control over what actions an agent can perform, all from within the MCPX interface.
Using the Agent Access Modal
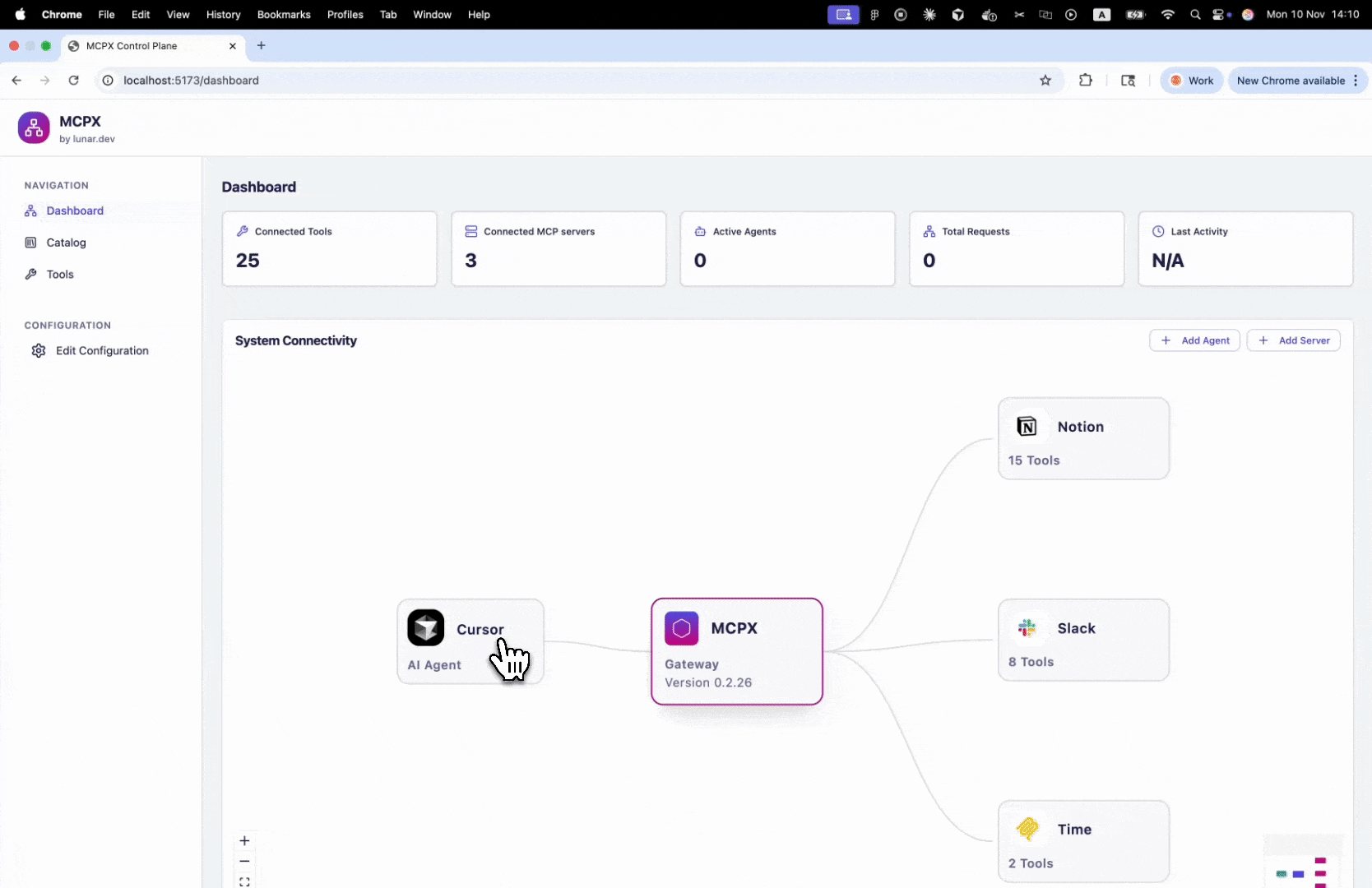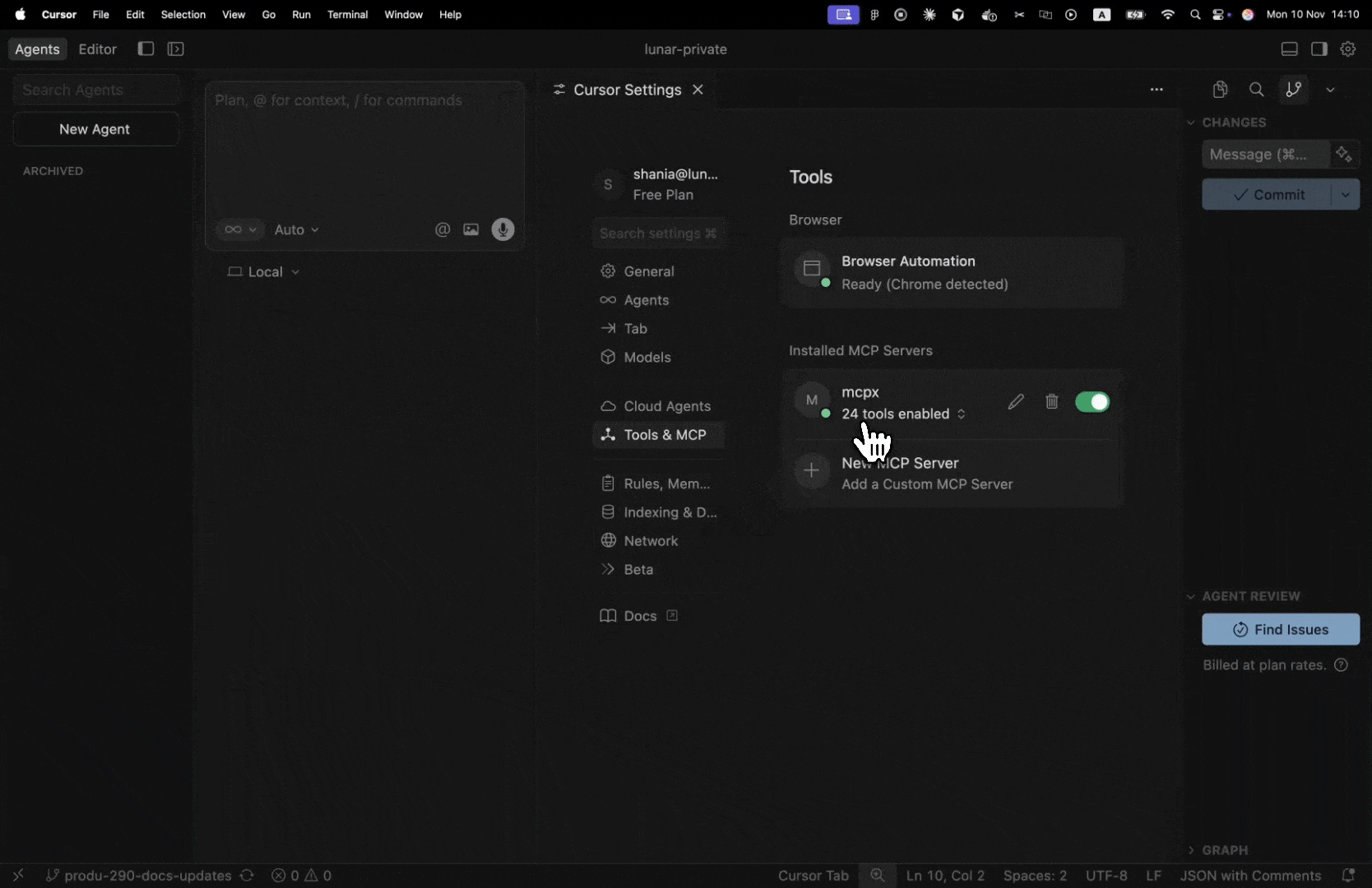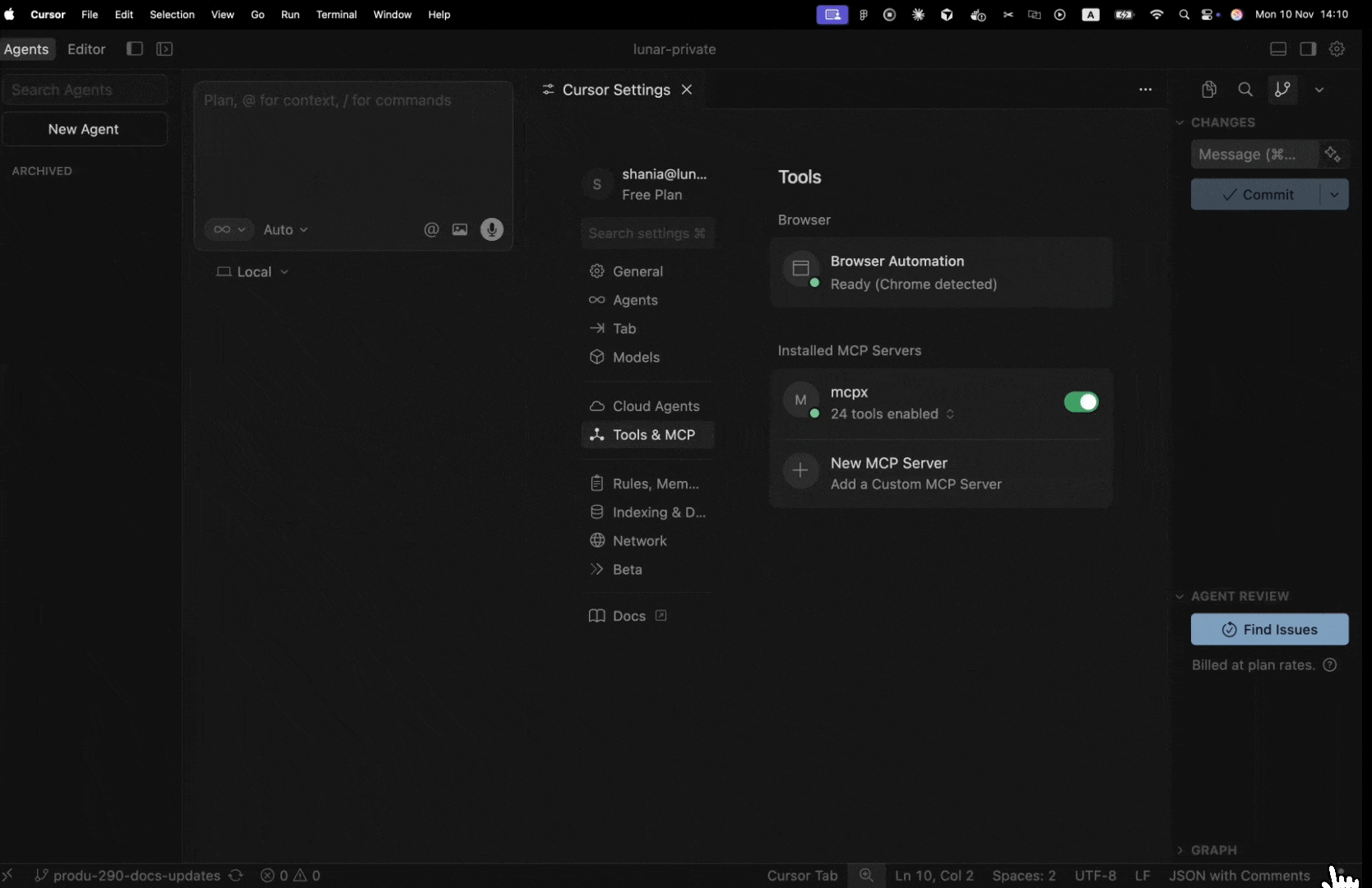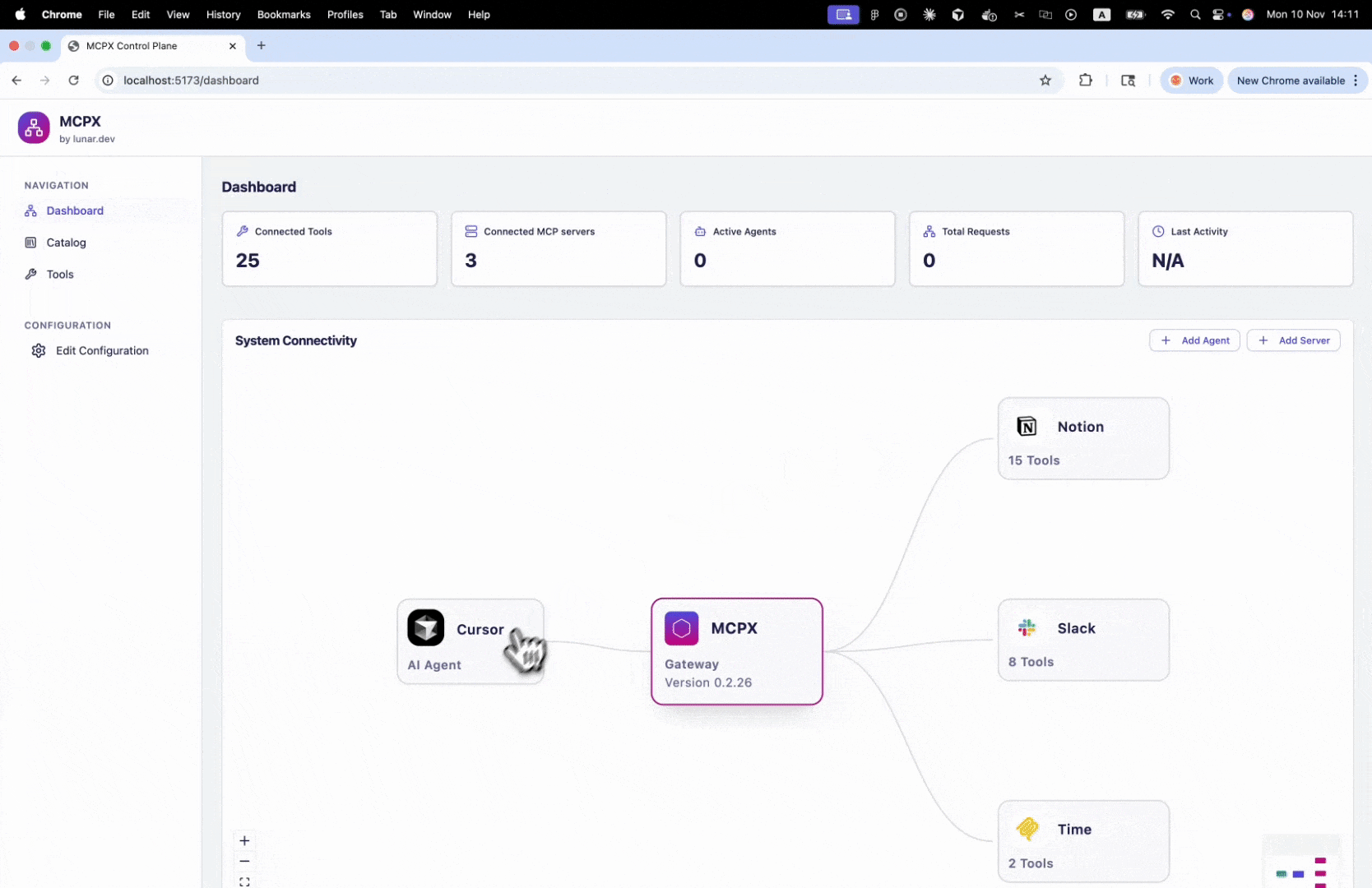
- Open the MCPX UI Dashboard.
- Select an agent to open its settings modal.
- In the Tools Access section, choose one of two options:
- All Server Tools — the agent can use all available tools.
- Tool Groups — you can enable or disable specific tool groups.
- Toggle access per group or service as needed.
Default Access Rules
If you haven’t created any tool groups yet, All Server Tools is automatically enabled. As soon as tool groups exist, you can select which tool groups the agent can access. This provides flexibility while maintaining secure defaults.
Learn more about creating and managing tool groups in Tool Groups.
MCPX follows the MCP Specifications for List Changed notifications, meaning that when MCPX recognizes that a user made changes to a tool it notifies the client by sending a list_changed notification. However, not all clients support this notification yet, so you may need to restart your client in order to see the updated tool access.