Static OAuth Support
Static OAuth support in MCPX extends the existing Client Credentials Flow by adding support for Device Flow Authorization (OAuth 2.0 Device Authorization Grant). Users can now configure either authentication method depending on their needs.
By default, MCPX includes a single default config for GitHub, however user-supplied configuration will override pre-defined defaults.
How to use
Add the static OAuth snippet to your app.yaml to enable OAuth with device flow. Then restart your MCPX server and log in through the browser with the device code shown in the UI.
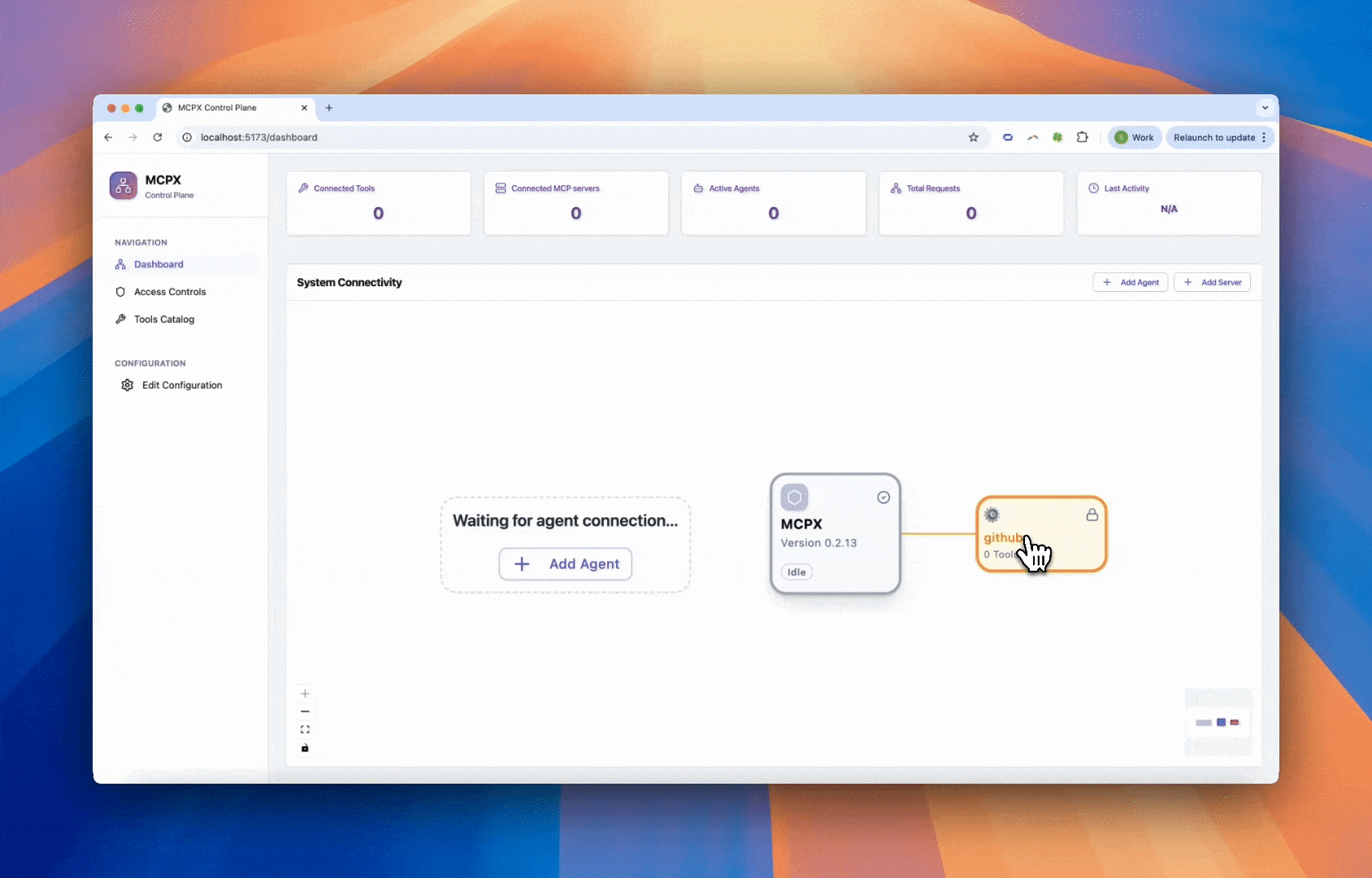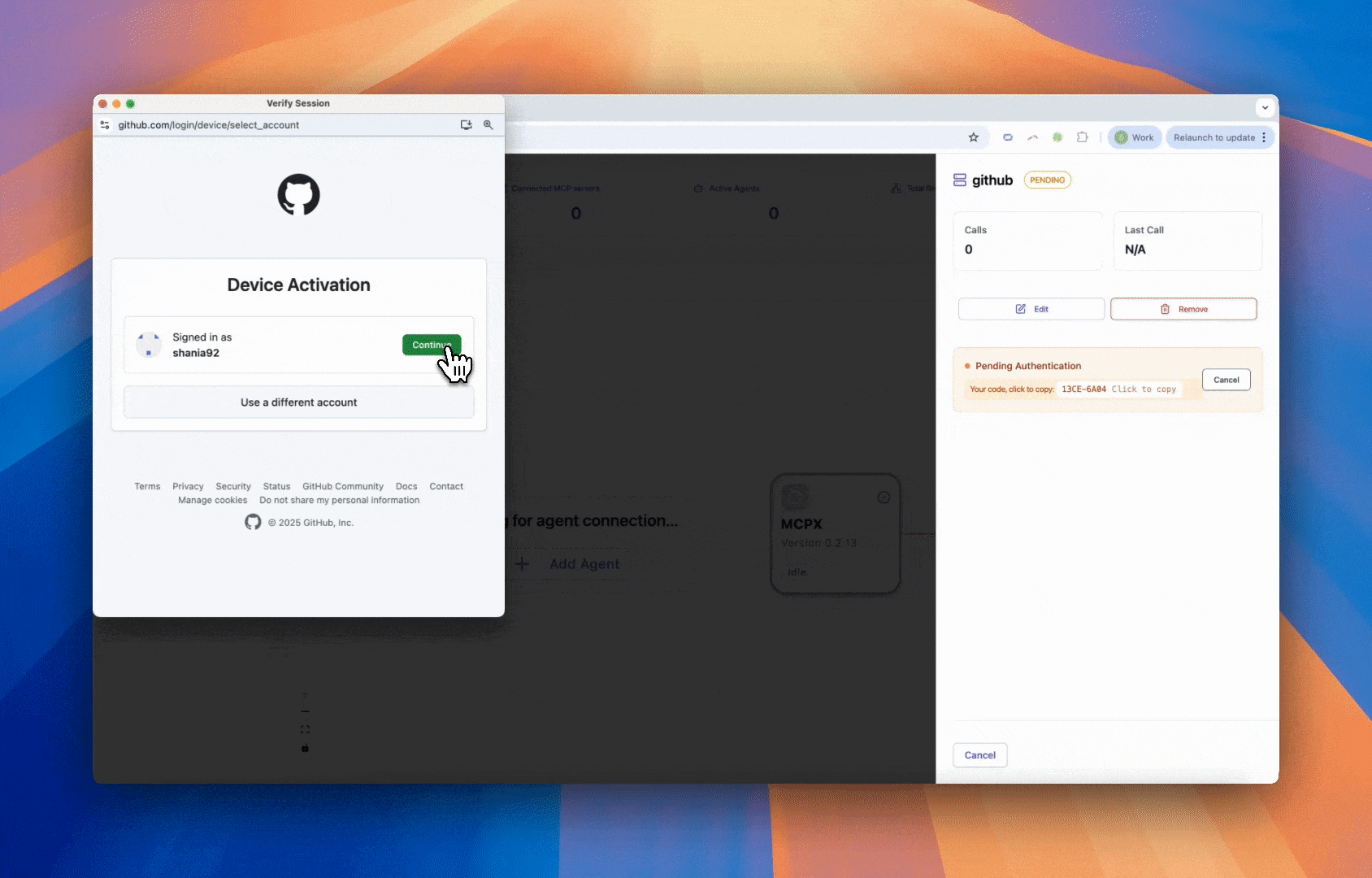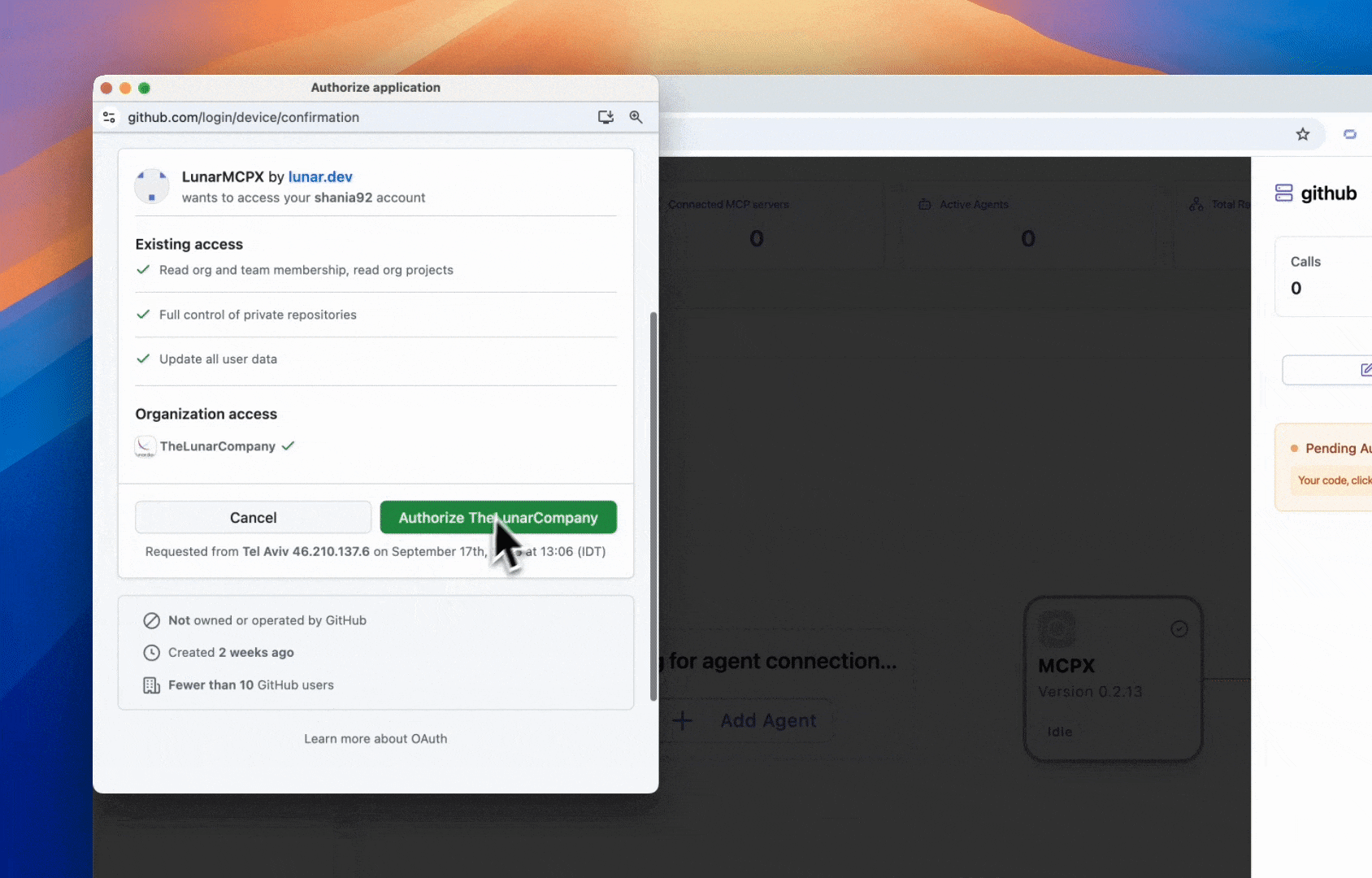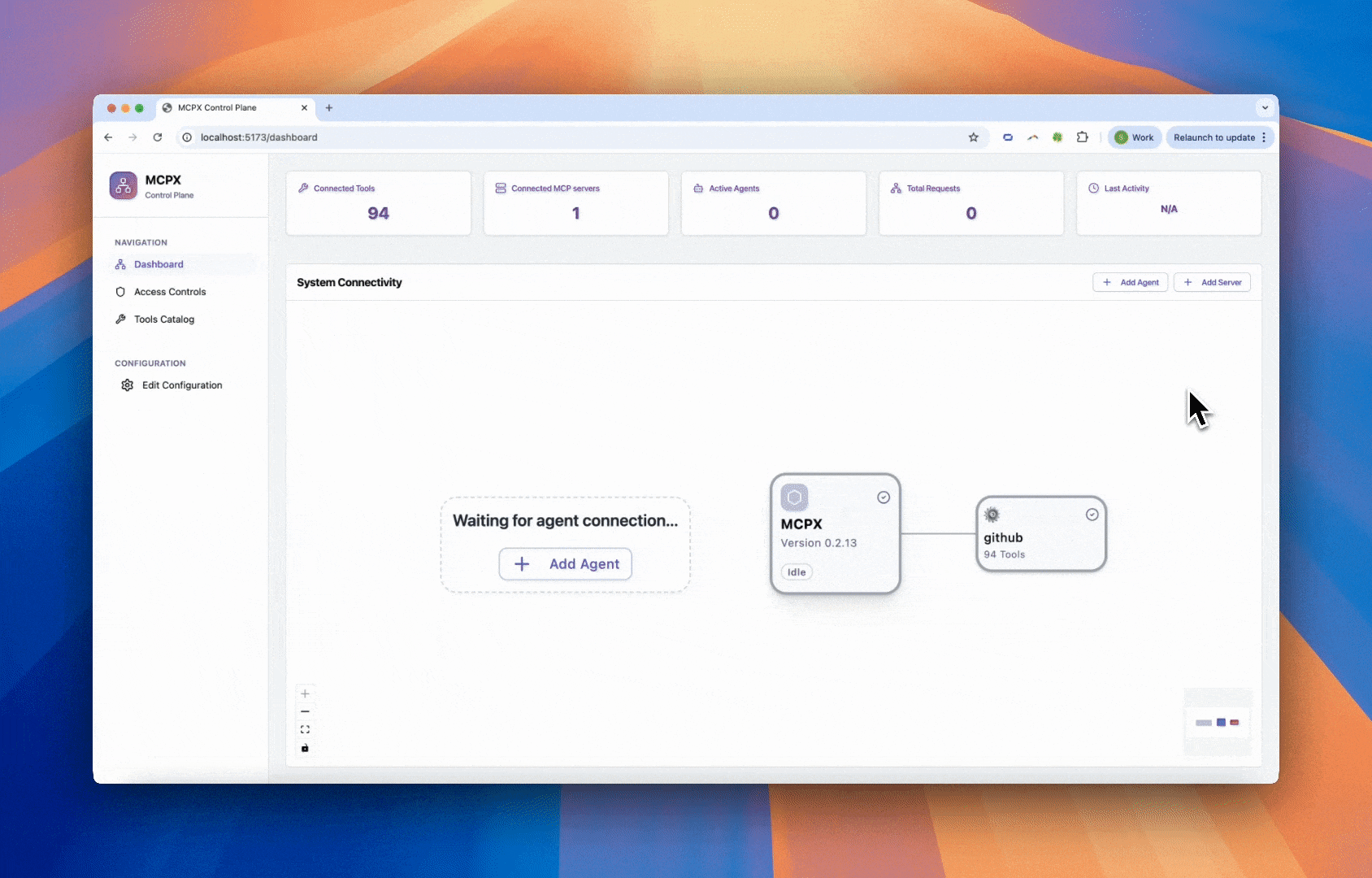
Choosing the Right Flow
- Client Credentials Flow is suitable when users provide their own organizational or personal OAuth app credentials.
- Device Flow is useful when you want to avoid distributing a client secret (for example, with a new GitHub OAuth app) or override defaults.
Client Credentials Flow
Example: private GitHub apps using a client ID and secret.
staticOauth:
mapping:
github.com: github-static
api.github.com: github-static
providers:
github-static:
authMethod: client_credentials
credentials:
clientIdEnv: "GITHUB_OAUTH_CLIENT_ID"
clientSecretEnv: "GITHUB_OAUTH_CLIENT_SECRET"
scopes: [repo, user, read:org]
tokenAuthMethod: client_secret_post
Device Flow
Example: public GitHub apps where no secret is needed.
staticOauth:
mapping:
github.com: github-device
api.github.com: github-device
providers:
github-device:
authMethod: device_flow
credentials:
clientIdEnv: "GITHUB_DEVICE_CLIENT_ID"
scopes: [repo, user, read:org]
endpoints:
deviceAuthorizationUrl: https://github.com/login/device/code
tokenUrl: https://github.com/login/oauth/access_token
userVerificationUrl: https://github.com/login/device
Parameters
mapping
Type: List of Map
Maps a domain or host to a provider key defined under providers and associates the domain with a provider key.
providers
Type: Map of objects
A dictionary of provider configurations. Each entry corresponds to a single OAuth provider to define the authentication details for each provider key. Each provider must specify an authMethod, either client_credentials or device_flow.
client_credentials Parameters
Used for private or organizational OAuth apps that include both a client ID and client secret.
authMethod
Type: "client_credentials"
Required: Yes
Selects the client credentials flow.
clientIdEnv
Type: string
Required: Yes
Environment variable name that holds the OAuth client ID.
clientSecretEnv
Type: string
Required: Yes
Environment variable name that holds the OAuth client secret.
scopes
Type: string
Required: Yes
OAuth scopes requested for this provider.
tokenAuthMethod
Type: enum
Required: Yes
How client credentials are sent to the token endpoint. Optional Inputs:
client_secret_basicclient_secret_postclient_secret_jwtprivate_key_jwttls_client_authself_signed_tls_client_auth
device_flow Parameters
Used for public OAuth apps where no client secret is required. Users authenticate by entering a code on a verification page.
authMethod
Type: "device_flow"
Required: Yes
Selects the device flow authorization method.
clientIdEnv
Type: string
Required: Yes
Environment variable name that holds the OAuth client ID.
scopes
Type: string[]
Required: Yes
OAuth scopes requested for this provider.
deviceAuthorizationUrl
Type: string
Required: Yes
URL of the provider’s device authorization endpoint.
tokenUrl
Type: string
Required: Yes
URL of the provider’s token endpoint.
userVerificationUrl
Type: string
Required: Yes
URL users visit to enter the device code and complete authorization.